I’ve been meddling with infosec for several years now, and have built my fair share of servers. I’ve always been fascinated by the various open source security tools, such as Mod Security, Tripwire, Fail2ban and the likes and enjoyed tinkering with them. Despite this fascination, i would always get bogged down with ongoing management, log monitoring and a general lack of visibility into the whole picture. Tripwire logs were hard to comb through, modsecurity logs were difficult to decipher, and the general process of fine tuning these tools was often just abandoned.
I always dreamt of of having a simple and effective interface to manage, view and monitor all the good ness these open source tools have to offer. After much tinkering, failing and generally questioning life choices, i’ve finally come up with something i’m happy to work with, and improves my ability to monitor servers through unified mysql logging. I wanted to document and share the process in case others find this useful. If you find images like this combined with the words “open source” and “security” exciting, then read on.
What we’re trying to Achieve
Our end goal is to setup an Ubuntu server, running the following open source security software:
- Mod Security with MySQL logging with CRS
- Fail2ban with MyQL logging an expanded set of Jails
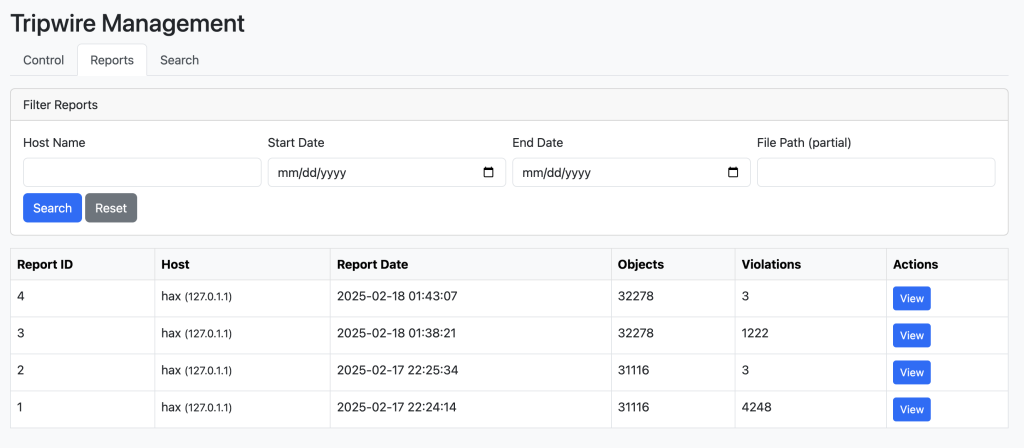
- Tripwire with MySQL Database report logging
- Cloudflare API integration with autobanning using fail2ban
- Web interface to manage all of this goodness